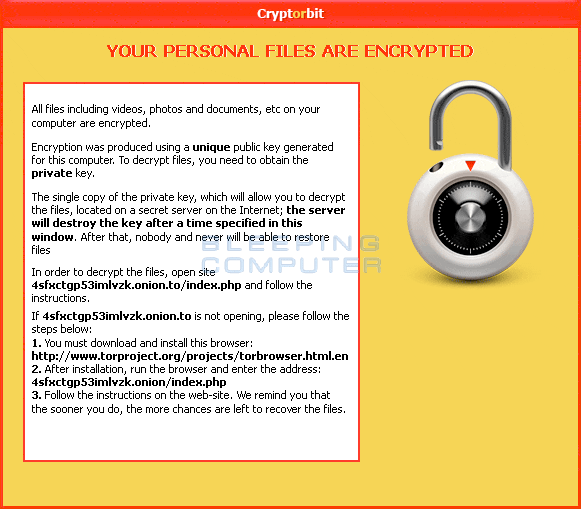
A new ransomware program called CryptorBit, which is similar to CryptoLocker and CryptoDefense, is being installed on Windows computers through fake flash updates and other social engineering tactics, warns Stu Sjouwerman, CEO of security awareness training company KnowBe4.
The malware, also known as HowDecrypt, presents itself in the form of a Flash update or anti-virus program, which unsuspecting users may install believing it to be a legitimate Adobe update or anti-virus program. It then corrupts the first 512 or 1024 bytes of any data file it finds, regardless of the file extension, and will only decrypt the files after $500 in bitcoin has been paid, according to Sjouwerman.
“To add insult to injury, the cybercrims are also installing so-called cryptocoin miner software which utilizes the victim’s computer to mine digital coins such as Bitcoin, which will get deposited in the malware developer’s digital wallet, making them even more money,” said Sjouwerman in his blog post. CryptorBit also reportedly has the ability to bypass Group Policy settings designed to protect against similar ransomware attacks.
Bleepingcomputer.com reported that once files are encrypted on a computer, the malware creates two files in each folder where a file was encrypted, “HowDecrypt.txt” and “HowDecrypt.gif.” In each file are instructions on how to access the payment site so that a user can send the ransom. The payment site is only accessible through the Tor network by visiting 4sfxctgp53imlvzk.onion, and the ransom can only be paid in Bitcoin.
The following are a few Bitcoin addresses believed to be associated with CryptorBit, which have received a total of ~40 bitcoins:
https://blockchain.info/address/15JTKDkU4U6Tn5MBc9Pt52mMzXDmvmaanR
https://blockchain.info/address/12GZoiAdcUubEwtArg1MApKB5uazpVneih
https://blockchain.info/address/1CgMiXHjLFUM3E79USnVM5Sikf5j9gTdXy
https://blockchain.info/address/17FSkXDULjtK6R9G3cpwmLMYbWRZJ9c8vZ
And don’t expect your anti-virus software to catch CryptorBit. Brian Dye, senior vice president for information security at security company Symantec, called commercial anti-virus software “dead.” Dye estimates that anti-virus software only catches 45 percent of attacks and leaves users vulnerable.
There are a few recovery options for those infected with CryptorBit, including a program called DecrypterFixer, which is designed to assist in the restoration of encrypted files. The first step in recovery is to use the System Restore function, which uses shadow copies of files to restore previous versions of computer files from before they were encrypted. For this to work, the System Restore function has to have been enabled and run at least once prior to the encryption.
The other option is to install a program called DecrypterFixer, created by Nathan Scott, which can recover corrupted PST, JPG, PDF, MP3, DOC, and XLS files.
Bleepingcomputer.com explains here how to use native Windows Previous Versions, Shadow Explorer or DecrypterFixer to restore files and folders.
Sjouwerman offers the following advice on how to avoid becoming a victim of the CryptorBit ransomware:
1) Backup, backup, backup and test your restore procedure on a very regular basis.
2) Don’t rely on just antivirus as they normally run 6 hours behind attacks like this, enough for the bad guys to get in and wreak havoc. See Virus Bulletin’s testing info.
3) Don’t open anything suspicious. Use extra care to avoid phishing links and attachments. If you didn’t request it, don’t open it.
4) If you do fall prey to CryptorBit, wipe the infected machine(s), rebuild from the ground up, and restore the files from the most recent backup. If there are no backups, try to restore the files from Shadow Volume Copies. If these are not available, you can try a utility called DecrypterFixer written by Nathan Scott.